picoCTF 2018: HEEEEEEERE'S Johnny!

This post marks the beginning of what I hope will become a long series of posts detailing my solutions to various notable problems from picoCTF 2018. My team, Open Sorcery, did fairly well, barely being edged out of the top 100 as the competition ended. I’ll try to avoid the very simple problems and focus more on problems that fewer people solved.
The Problem
Okay, so we found some important looking files on a linux computer. Maybe they can be used to get a password to the process. Connect with
nc 2018shell1.picoctf.com 5221. Files can be found here: passwd shadow.
passwd and shadow are both links to files without extensions.
Running the given nc command results in the following login prompt:
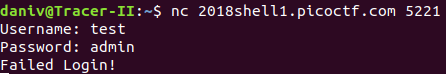
Hints
2 hints are provided for this problem. The first reads:
If at first you don’t succeed, try, try again. And again. And again.
The second reads:
If you’re not careful these kinds of problems can really “rockyou”.
My Solution
The challenge shared a name with John the Ripper, which I believed was no coincidence. Furthermore, research of the term rockyou led me to a file called rockyou.txt, filled with millions of common passwords. I combined these two resources in order to run John the Ripper on shadow:
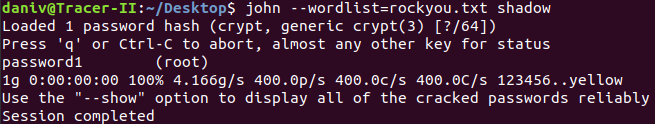
As you can see, John successfully cracked the password password1. It didn’t reveal any usernames, so I simply tried admin and then root, two very common superuser usernames. In the end, root was the correct username and the program gave me the flag:
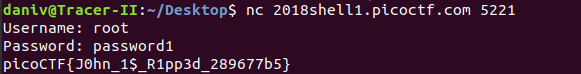
I was left with the correct flag, picoCTF{J0hn_1$_R1pp3d_289677b5}.